Hey Folks
Here again with another security topic with Fetian Fido. And once again Fetian devices proved their excellent quality and stability.
For this I choose Fetian
K33 - AllinPass FIDO Security Key – FEITIAN (ftsafe.com)
and
K39 - Single-button FIDO Security Keys | FEITIAN (ftsafe.com)
Use case
In an organization following changes needs to be implemented.
1. Update the password policy
2. Update the user session time out to 30 minutes
Once these changes being implemented, the following issues need to be addressed
1. Users' complaint new passwords need to be so long
2. Users complain sessions time out makes them work so much slower with the longer passwords
3. Etc...
Solution
One of my friends reached out to me to help solve this problem. All I could think of was using passwordless auth with FIDO devices. We have decided to use Fido2 keys for better security and flexibility for the users.
The FIDO (Fast IDentity Online) Alliance helps to promote open authentication standards and reduce the use of passwords as a form of authentication. FIDO2 is the latest standard that incorporates the web authentication (WebAuthn) standard.
According to MS Docs
"FIDO2 security keys are an unphishable standards-based passwordless authentication method that can come in any form factor. Fast Identity Online (FIDO) is an open standard for passwordless authentication. FIDO allows users and organizations to leverage the standard to sign in to their resources without a username or password using an external security key or a platform key built into a device. "
Users can register and then select a FIDO2 security key at the sign-in interface as their main means of authentication. These FIDO2 security keys are typically USB devices, but could also use Bluetooth or NFC. With a hardware device that handles the authentication, the security of an account is increased as there's no password that could be exposed or guessed.
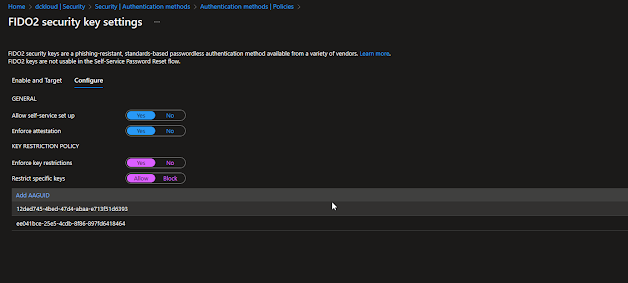
The following settings were configured in Azure Active Directory for our Fido solution and provided users access to configure the devices by themselves
AAGuides for Fetian can be found here
Products – FIDO Security Keys (ftsafe.com)
Why Feitian
A few months back I did another review of one of the Fetian products and was impressed a lot. And when looking for a proper fit k33 and k39 (successor of k34) caught my eye. Also, Fetian Fido2 keys are endorsed by Microsoft as a supported product with Microsoft Services It's based in Beijing, China. They're active in over 100 regions. Most all the devices are really straightforward to configure with most of the vendor instructions. So far I found 1 device which is slightly different from other devices is AllinPass (k33) has some extra steps and requires USB C connectivity to a PC to set up the fingerprints
K33 was proposed to high-risk users, The AllInPass is a Bluetooth-enabled security key with a built-in biometric fingerprint reader, all packed into the size of a keyless car key. That's definitely not the case here, Fetian has clearly put time and effort into industrial design, and it pays off.
K39 was proposed to all the other users, K39 is a simple USB stick-style key with a USB C interface. Which is really easy to use and they can have it in their keychains. Personally, I like K39 because of the below reasons.
- Easy to configure
- Unlike other keys, it has some muscle to it
- USB C gives more flexibility with devices (Laptop or Mobile)
- etc.
You must be wondering why we chose 2 mobile-friendly keys from Fetian. We wanted to provide the opportunity for the users to use these keys with their company-provided mobile devices as well.
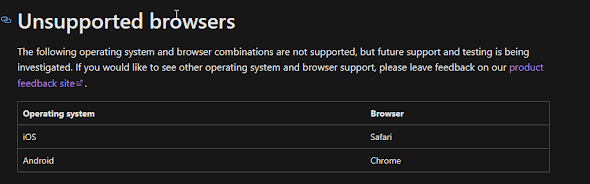
But at the moment Microsoft does not support FIDO with either android or iOS, but it's in development
But as per Microsoft these are under development. So, we want users to use the keys on mobile devices soon after they releases this feature for mobile devices
Conclusion
In summary,- Fetian K33 and K39 devices are two awesome productions that match perfectly with our solution
- Both these Fetian devices are mobile friendly that help the organization in the long run and they don't need to change to another set of Fido devices in future
- Most organizations are looking at mobile Fido support by Microsoft, even google supports it. I think this should be worked on as a priority.
- Why you need to consider Fetian... Well, I have outlined many advantages and points throughout my blog :D




Comments
Post a Comment